Navigation: Configuration > Configuration Guide (Web Mode) > Advanced Configuration >
The unified gateway can encrypt SIP signaling using TLS to improve the security and reliability of voice communication.
Context
When an IP phone or IAD registers with the unified gateway using SIP, or when the unified gateway initiates a call to a peer office through a SIP trunk, the communication parties send SIP signaling to negotiate the data transmission address and port number. To ensure the security of data communication, you can encrypt SIP signaling using TLS.
TLS is a cryptographic protocol that provides communication security between two communication application programs, ensuring data confidentiality and integrity. When transmitting signaling using TLS, two parties must pass certificate authentication to ensure the communication reliability. The two parties interacting using TLS are defined as a TLS server and a TLS client to facilitate the description of the authentication process. The client and server must possess corresponding certificates and private keys and use the same authentication mode.
ϒ⁄Certificates and private keys
Certificates and private keys are authentication credentials for the TLS server and client. The unified gateway and UScale 78xx/79xx series IP phones are provided with built-in certificates and privates keys before delivery. The unified gateway and IP phones can authenticate each other using these built-in certificates and privates keys. After the deployment, it is recommended that the customer generate or apply for the TLS certificates from an official organization.
§rootcert.pem: root certificate
§servercert.pem: server certificate
§serverkey.pem: server private key
§clientcert.pem: client certificate
§clientkey.pem: client private key
ϒ⁄Authentication mode
The unified gateway supports the following authentication modes. The TLS server and client must use the same authentication mode.
§Server authentication: For each signaling interaction, the server sends the server certificate and root certificate to the client for authentication.
§Client authentication: For each signaling interaction, the client sends the client certificate and root certificate to the server for authentication.
§Anonymous authentication: For each signaling interaction, the server and client negotiate a key for encrypting data.
The following table lists the scenarios of signaling encryption using TLS.
Table 1 Scenarios of signaling encryption using the TLS
Scenario |
Description |
Port |
Encrypted SIP registration |
IP phones and IADs register with the unified gateway in encrypted mode using TLS. In this scenario, the unified gateway must be the TLS server while IP phones and IADs must be TLS clients. NOTE: ϒ⁄The UScale 78xx series IP phones support only anonymous authentication mode. The UScale 79xx series IP phones support anonymous and server authentication modes. ϒ⁄The IADs support anonymous and server authentication modes. |
By default, the unified gateway, IP phones, and IADs use port 5060 for non-encrypted registration and port 5061 for encrypted registration. NOTE: In the scenario of encrypted SIP registration, IADs can register with a SIP server only through port 5061. If IADs are deployed on the network, you are advised to use the default port 5061 as the encrypted SIP registration port on the unified gateway. |
Encrypted SIP trunk |
The unified gateway connects to a peer office through a SIP trunk using TLS. In this scenario, the unified gateway can be either the TLS server or client. However, if one party is configured as the TLS server, the other party must be configured as the TLS client. |
By default, the unified gateway uses port 5060 for non-encrypted SIP trunk connection. If you want to configure a TLS-encrypted SIP trunk, to avoid conflicts, do not use a port that has been used as an encrypted SIP registration port. You are advised to use port 5062 or 5063 for encrypted SIP trunk connection. |
(Optional) Loading Certificates and Private Keys
To use the certificates generated by the customer or applied from an official organization, load the certificates and private keys on all unified gateways and load the root certificate on all IP phones and IADs.
1.Prepare the certificates and private key files and rename them based on the information provided in the background section.
2.Load the certificates and private keys on unified gateways.
a.Set up an FTPS/TFTP server.
![]()
Using TFTP to transfer files may bring some security risks because TFTP is an insecure protocol. It is recommended that you use the FTPS protocol.
b.Load the root certificate, server certificate, and server private key on unified gateways functioning as TLS servers.
config download file rootcert mode <tftp|ftps>
config download file srvcert mode <tftp|ftps>
config download file srvkey mode <tftp|ftps>
c.Load the root certificate, client certificate, and client private key on unified gateways functioning as TLS clients.
config download file rootcert mode <tftp|ftps>
config download file cltcert mode <tftp|ftps>
config download file cltkey mode <tftp|ftps>
d.Set the password used for decrypting the private keys on the TLS server and client.
ϒ⁄If the created certificates have passwords:
§If the unified gateway is TLS server, run the config tls server switch enable password password command.
§If the unified gateway is TLS client, run the config tls client switch enable password password command.
ϒ⁄If the created certificates do not have passwords:
§If the unified gateway is TLS server, run the config tls server switch disable command.
§If the unified gateway is TLS client, run the config tls client switch disable command.
![]()
If the private keys provided by unified gateways are used, the password is oocag7Uj.
e.Run the reboot command to restart the device.
3.Load the root certificate on IP phones.
a.Log in to the web management system of an IP phone. (This section uses an UScale 79xx series IP phone as an example.)
b.Choose Advanced > Certificates.
c.In the Import Local Certificate area, click Browse for Root Certificate, and navigate to the root certificate, as shown in Figure 1.
Figure 1 Loading the root certificate on an IP phone
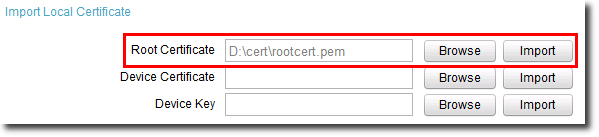
d.Click Import for Root Certificate.
e.Restart the IP phone as prompted.
4.Load the root certificate on IADs.
a.Log in to the web management system of an IAD.
b.Choose Maintenance > TLS Certfile Upgrade.
c.Select a transmission mode, click Browse, and navigate to the root certificate, as shown in Figure 2.
Figure 2 Loading the root certificate on an IAD
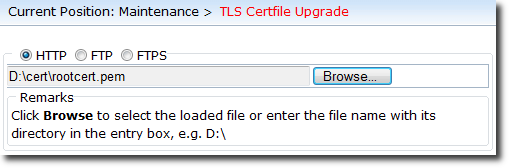
d.Click OK.
e.Choose Maintenance > Restart Device, and click Restart Device to restart the device.
Configuring Encrypted SIP Registration
This section assumes that you need to configure encrypted SIP registration on an IP phone and an IAD so that they can register with the unified gateway in encrypted mode using TLS, and assumes that user numbers have been allocated. Configure encrypted SIP registration onsite based on your own data plan.
Figure 3 Network for configuring encrypted SIP registration
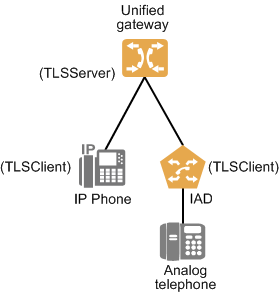
NE |
IP Address |
Role |
Signaling Transmission Port |
TLS Authentication Mode |
Unified gateway |
192.168.1.17 |
TLSServer |
5061 |
Server authentication |
IP phone |
192.168.1.100 |
TLSClient |
5061 |
Server authentication |
IAD |
192.168.1.150 |
TLSClient |
5061 |
Server authentication |
ϒ⁄Check SIP registration parameters on the unified gateway.
1.Log in to the device using a command-line tool.
2.Run the show sip parameter command and view the parameters listed in the following table.
Parameter |
Description |
UdpSrvPort |
UDP registration port for IP terminals. The default value is 5060. If an IP phone or IAD registers with the unified gateway using UDP, enter this port when configuring the SIP server on the IP phone or IAD. |
TcpSrvPort |
TCP registration port for IP terminals. The default value is 5060. If an IP phone or IAD registers with the unified gateway using TCP, enter this port when configuring the SIP server on the IP phone or IAD. |
TlsSrvPort |
TLS registration port for IP terminals. The default value is 5061. If an IP phone or IAD registers with the unified gateway using TLS, enter this port when configuring the SIP server on the IP phone or IAD. You are advised to use the default value because IADs can register with a SIP server only through port 5061 in the scenario of encrypted SIP registration. |
TlsAuthMode |
TLS authentication mode. The default value is Anonymous. The options are as follows: ϒ⁄anonymous: anonymous authentication ϒ⁄Server_auth: server authentication ϒ⁄Client_auth: client authentication |
TlsConnMode |
TLS connection mode. The default value is Long. The options are as follows: ϒ⁄Long: A TLS connection is kept alive once it is set up. All SIP interactions are performed on the initial TLS connection. ϒ⁄Short: A TLS connection is set up only when there are SIP messages to transmit. After the messages are transmitted, the connection is released. |
1.Verify that the TlsSrvPort value is 5061 as planned. If not, run the config modify sip parameter command to modify the parameter.
![]()
ϒ⁄In the config modify sip parameter command, parameters srvport and tlsport correspond to UdpSrvPort and TlsSrvPort respectively.
ϒ⁄You can also log in to the web management system to modify the parameters. Specifically, choose System > Device Management and click Configure next to SIP Server.
ϒ⁄Set SIP registration parameters on the IP phone.
1.Log in to the web management system of the IP phone.
2.Choose Advanced > Network. In the Network Security area, set SIP Transport and TLS Certificate Issuer and click Save.
![]()
The issuer of the built-in root certificate on an IP phone is OpenVox Enterprise UC&C ProductLine CA. If a custom certificate is used, select the custom certificate that has been loaded.
3.Choose Advanced > Others, select a TLS authentication mode, and click Save, as shown in Figure 5.
Figure 5 Selecting a TLS authentication mode on an IP phone
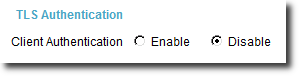
![]()
If you select Disable, the anonymous authentication mode takes effect. The TLS authentication mode selected here must be the same as that configured on the SIP server.
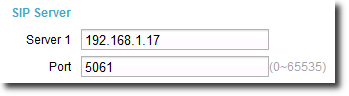
4.Choose Advanced > Server, configure the SIP server, and click Save, as shown in Figure 6. Note that the port number of the SIP server must be the same as the TlsSrvPort value on the unified gateway.
Figure 6 Configuring the SIP server on an IP phone
ϒ⁄Set SIP registration parameters on the IAD.
1.Log in to the web management system of the IAD.
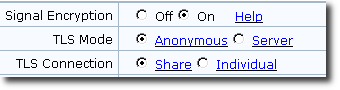
2.Choose Advanced Configuration > Signal and Media Encryption and set TLS parameters, as shown in Figure 7.
Figure 7 Enabling signaling encryption on an IAD
![]()
For the TLS Mode parameter, value Server indicates server authentication. The TLS authentication mode selected here must be the same as that configured on the SIP server.
3.On the page that is displayed, click save.
ϒ⁄Verify the configuration.
When the configuration is complete, view the SIP user status on the web management system of the IP phone and IAD. If the status is Registered, the configuration is successful.
Configuring an Encrypted SIP Trunk
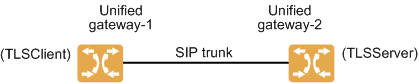
This section assumes that you need to configure an encrypted SIP trunk between two unified gateways, and assumes that office routes have been configured. Configure encrypted SIP trunks onsite based on your own data plan.
Figure 8 Network for configuring an encrypted SIP trunk
NE |
IP Address |
Role |
Signaling Transmission Port |
TLS Authentication Mode |
Unified gateway 1 |
192.168.1.17 |
TLSClient |
5062 |
Client authentication |
Unified gateway 2 |
192.168.1.18 |
TLSServer |
5063 |
1.Log in to the web management system of unified gateway 1.
2.Choose Trunk > Trunk Configuration > SIP.
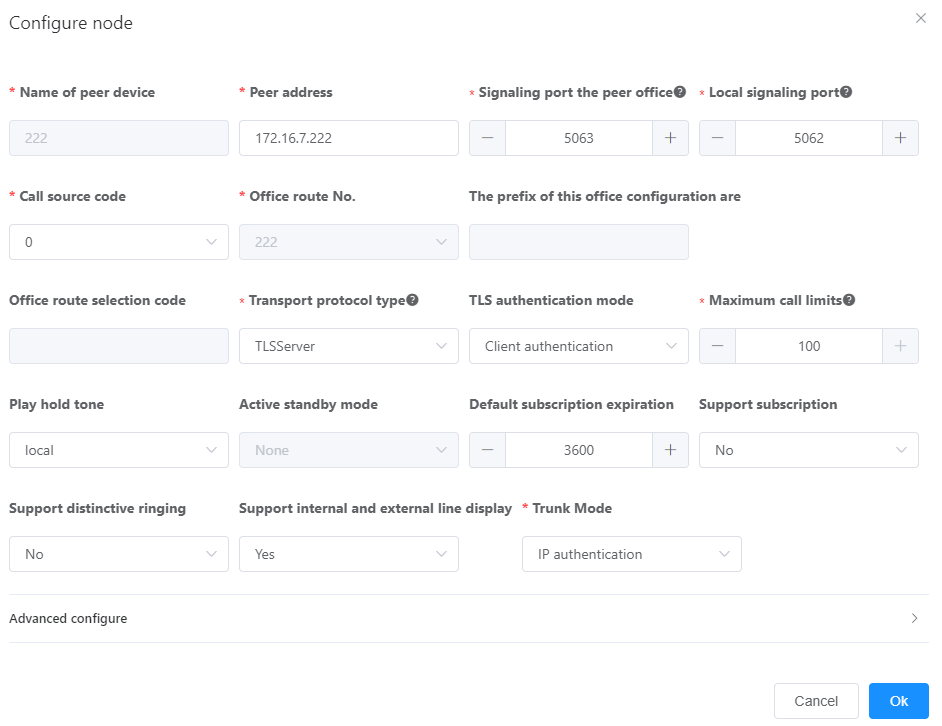
3.Click Add A Peer Office. Click the add icon or the red line connecting the the local office and set the parameters based on the network and parameter description, as shown in Figure 9.
Figure 9 Setting SIP trunk connection parameters on unified gateway 1
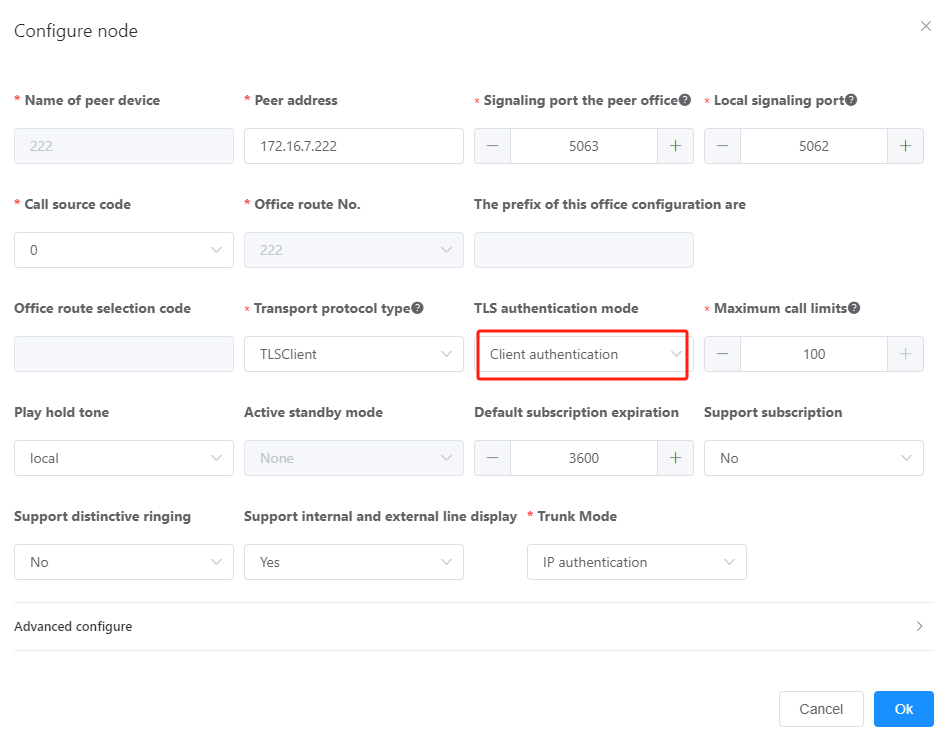
Table 2 describes the key parameters. For detailed description about the parameters, see the online help of the web management system.
Table 2 Key parameter description
Parameter |
Description |
Transmission protocol type |
The options include UDP, TCP, TLSServer, and TLSClient. For details about how to configure a SIP trunk using UDP or TCP, see Configuring a SIP Trunk. ϒ⁄TLSServer: TLS is used as the transmission protocol, and the local end is the TLS server. ϒ⁄TLSClient: TLS is used as the transmission protocol, and the local end is the TLS client. NOTE: The local office and peer office must be configured as a TLS server and a TLS client. |
Signaling port number of the peer office |
Signaling transmission port used by the peer office. The value must the same as the actual port used by the peer office. |
Signaling port number of the local office |
Signaling transmission port used by the local office. Use a port that has not been configured as an encrypted SIP registration port. You are advised to use port 5062 or 5063, or select an idle port by referring to Communication Matrix. |
TLS authentication mode |
TLS authentication mode of the SIP trunk. NOTE: The local office and peer office must use the same TLS authentication mode. |
1.Click OK.
2.Click Data Save in the upper right corner of the web management system.
![]()
The unsaved configurations will be deleted after the device is restarted.
3.Log in to the web management system of unified gateway 2 and configure the SIP trunk, as shown in Figure 10.
Figure 10 Setting SIP trunk connection parameters on unified gateway 2
4.Click OK.
5.Verify encrypted SIP relay.
After the configuration is completed, you can try to switch between the local game and the opponent game. If incoming and outgoing calls can be made normally, it indicates that the encrypted SIP relay connection is successful
Parent Topic: Advanced Configuration