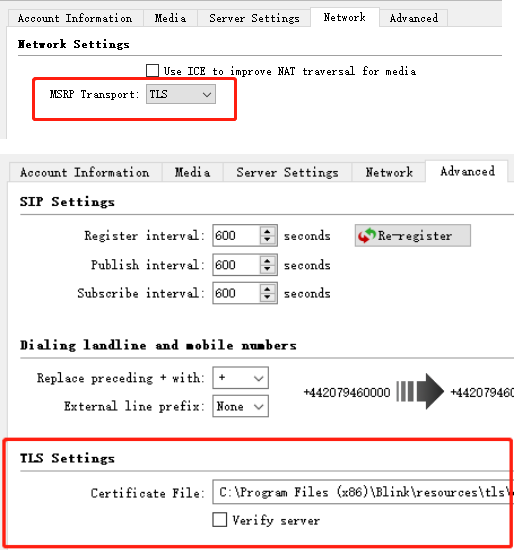
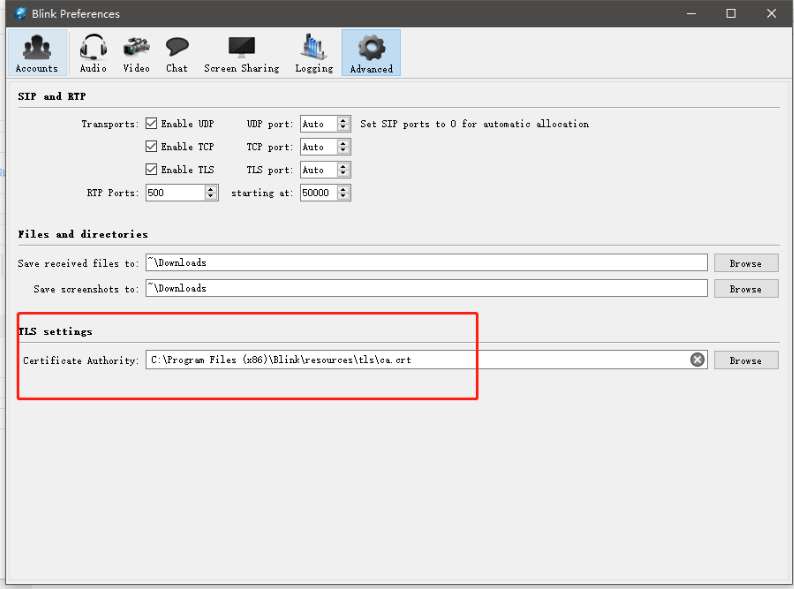
Analog Gateway FXS configure TLS and SRTP with Grandstream UCM6202
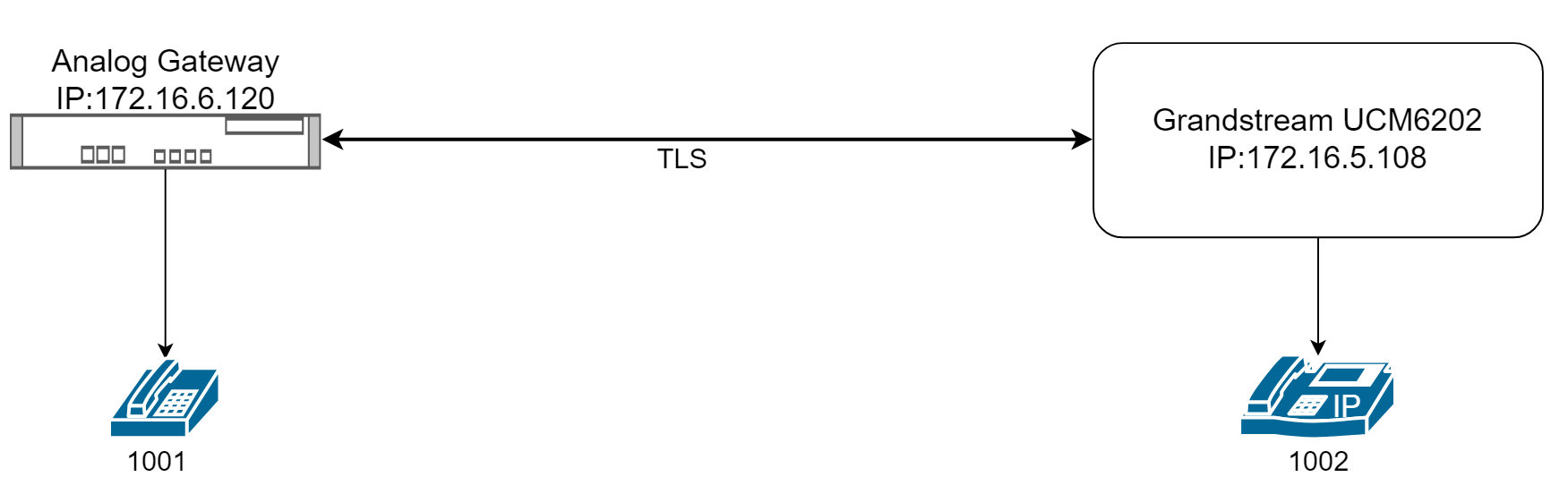
TLS (Transport Layer Security) is a network security protocol used to encrypt and secure data transmission over the internet. It establishes an encrypted channel between two communicating devices (e.g. server and client) to ensure that transmitted data is not intercepted or tampered with.
This article provides an example of configuring TLS between an Analog Gateway FXS and Grandstream UCM6202. After configuration, when phone 1001 on the Analog Gateway dials phone 1002 on Grandstream UCM6202, the data will be encrypted using TLS.
Note: The configuration example in this article uses a self-signed TLS certificate, which has relatively weak security. It is not recommended for use in formal production environments.
Step 1.Create extensions 1001 and 1002 on the Grandstream UCM6202
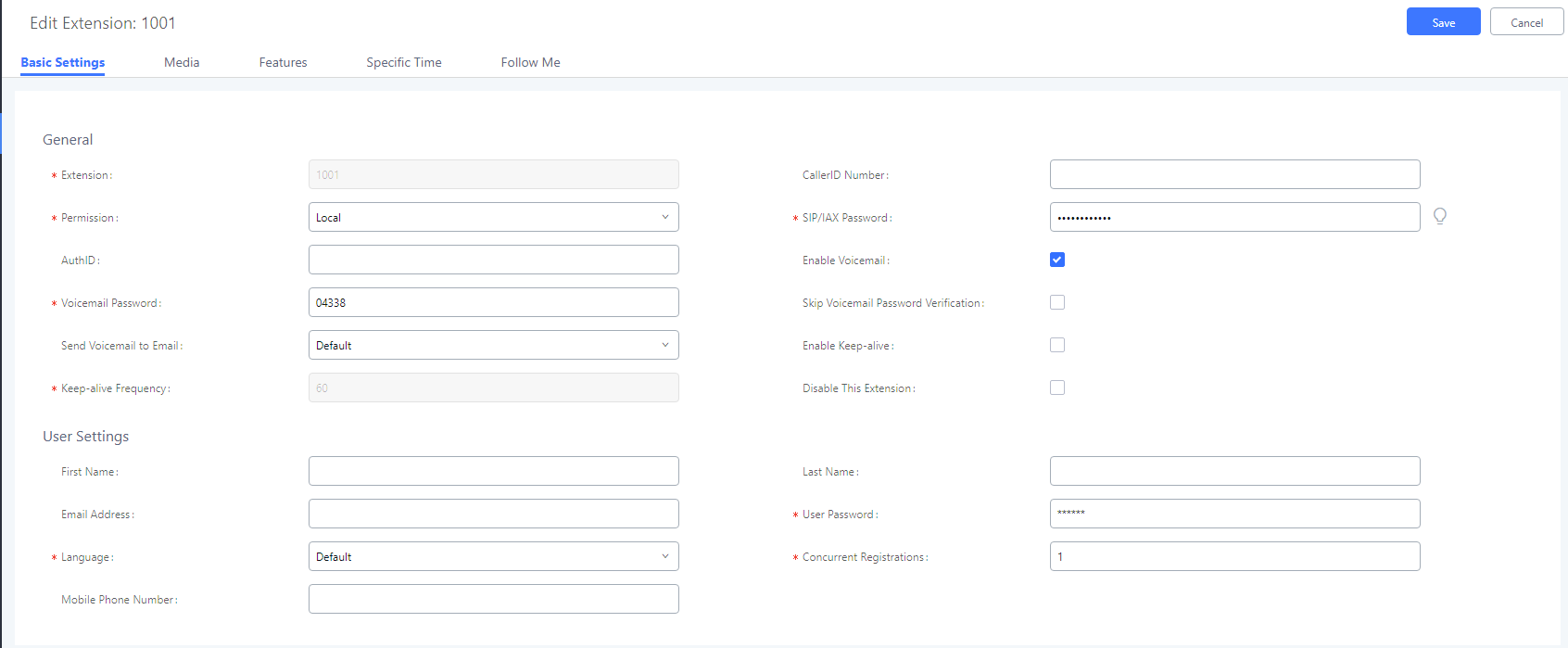
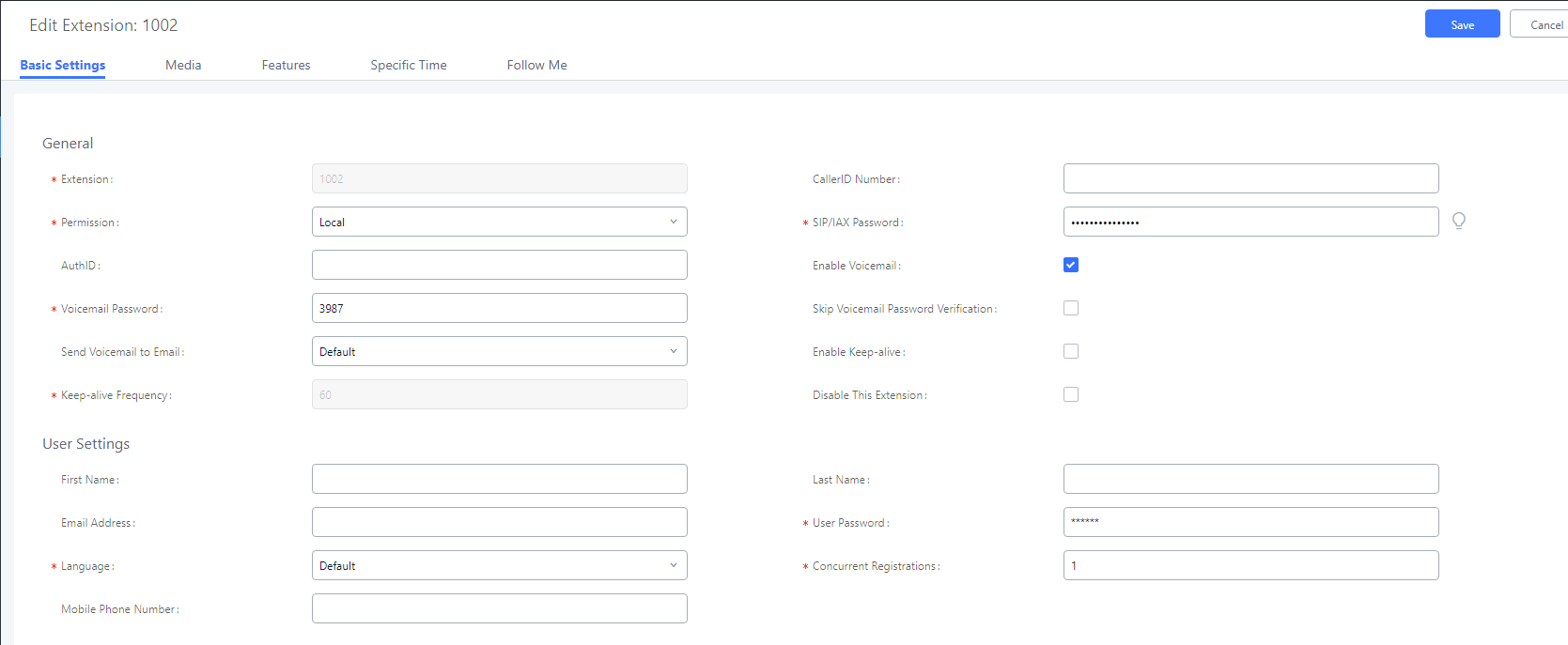
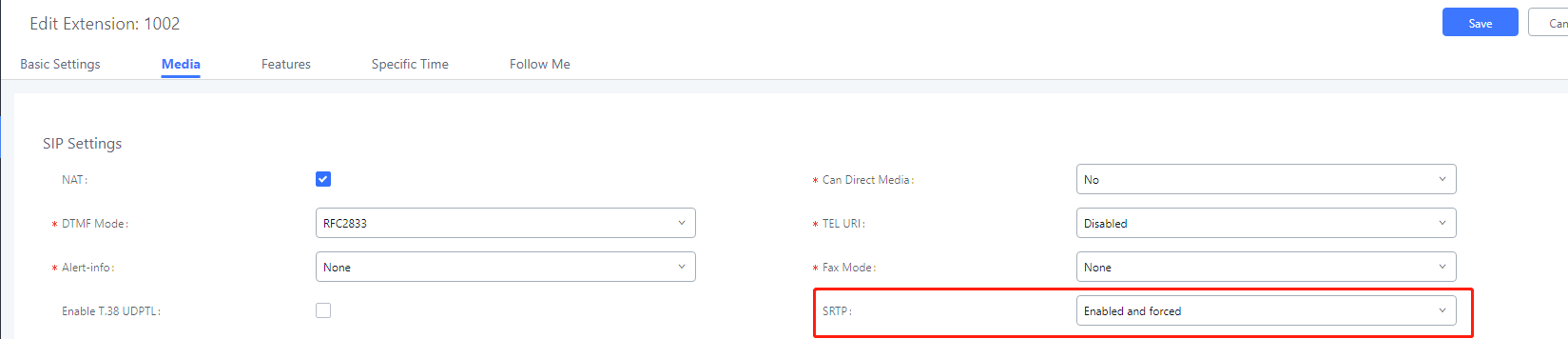
If you want use SRTP to encrypt the call, enable the SRTP.
Step 2. Use OpenSSL tool to generate server certificate and client certificates for 1001 and 1002.
To generate certificates, we need to use the openssl tool, including a root certificate and user certificates. Before the specific steps of generating certificates, we need to know several file formats related to certificates. All these formats belong to the PKCS (The Public-Key Cryptography Standards) standard:
.key file: Private key file, usually using RSA algorithm, the private key needs to be saved by yourself and does not need to be submitted to the CA organization.
.csr file: Certificate Signing Request (CSR) file, containing public key information. The CSR file is generated using your own private key.
.crt file: CA-certified certificate file, “certificate” abbreviation.
.crl file: Certificate Revocation List (CRL) file.
.pem file: A certificate format used for exporting and importing. This file is actually a combination of the .crt and .key files, similar to using .pfx on Windows, but different in that .pem uses base64 characters for storage while .pfx uses binary storage.
Steps to generate a CA root certificate:
1.Generate the CA private key (.key)
2.Generate a Certificate Signing Request (CSR) for the CA (.csr)
3.Self-sign the CSR to obtain the root certificate (.crt)
# Generate CA private key
openssl genrsa -out ca.key 2048
# Generate CSR
openssl req -new -key ca.key -out ca.csr
# Generate Self Signed certificate
openssl x509 -req -days 365 -in ca.csr -signkey ca.key -out ca.crtThe steps to generate a server-side certificate are as follows:
1.Generate a private key (.key).
2.Generate a certificate signing request (.csr).
3.Use the CA root certificate to sign the certificate and obtain a signed certificate (.crt) file.
# private key
openssl genrsa -des3 -out asterisk.key 1024
# generate csr
openssl req -new -key asterisk.key -out asterisk.csr
# generate certificate
openssl ca -in asterisk.csr -out asterisk.crt -cert ca.crt -keyfile ca.keyThe steps to generate a extension certificate are as follows:
1.Generate a private key (.key).
2.Generate a certificate signing request (.csr).
3.Use the CA root certificate to sign the certificate and obtain a signed certificate (.crt) file.
# private key
openssl genrsa -des3 -out 1001.key 1024
# generate csr
openssl req -new -key 1001.key -out 1001.csr
# generate certificate
openssl ca -in 1001.csr -out 1001.crt -cert ca.crt -keyfile ca.keyGenerate .pem file
cat asterisk.crt asterisk.key > asterisk.pem
cat 1002.crt 1002.key > 1002.pemStep 3.Upload certificate to Grandstream UCM6202.
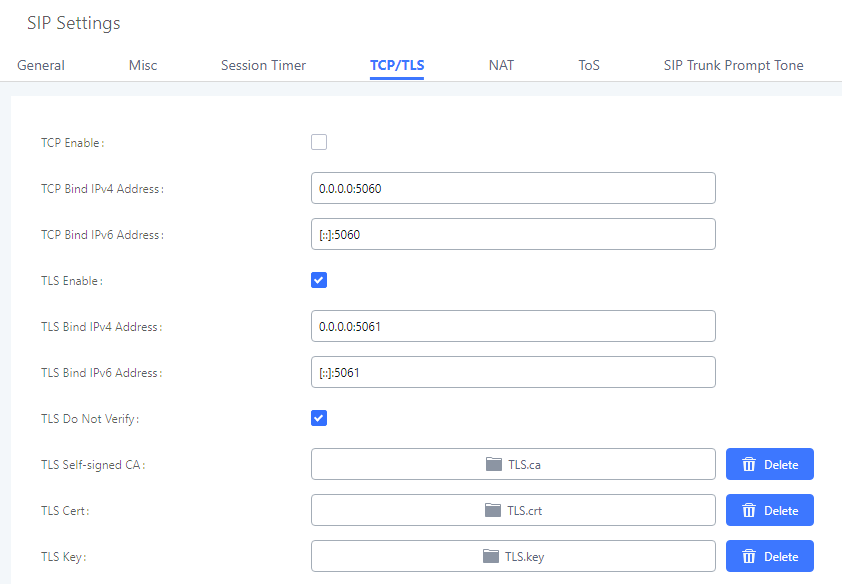
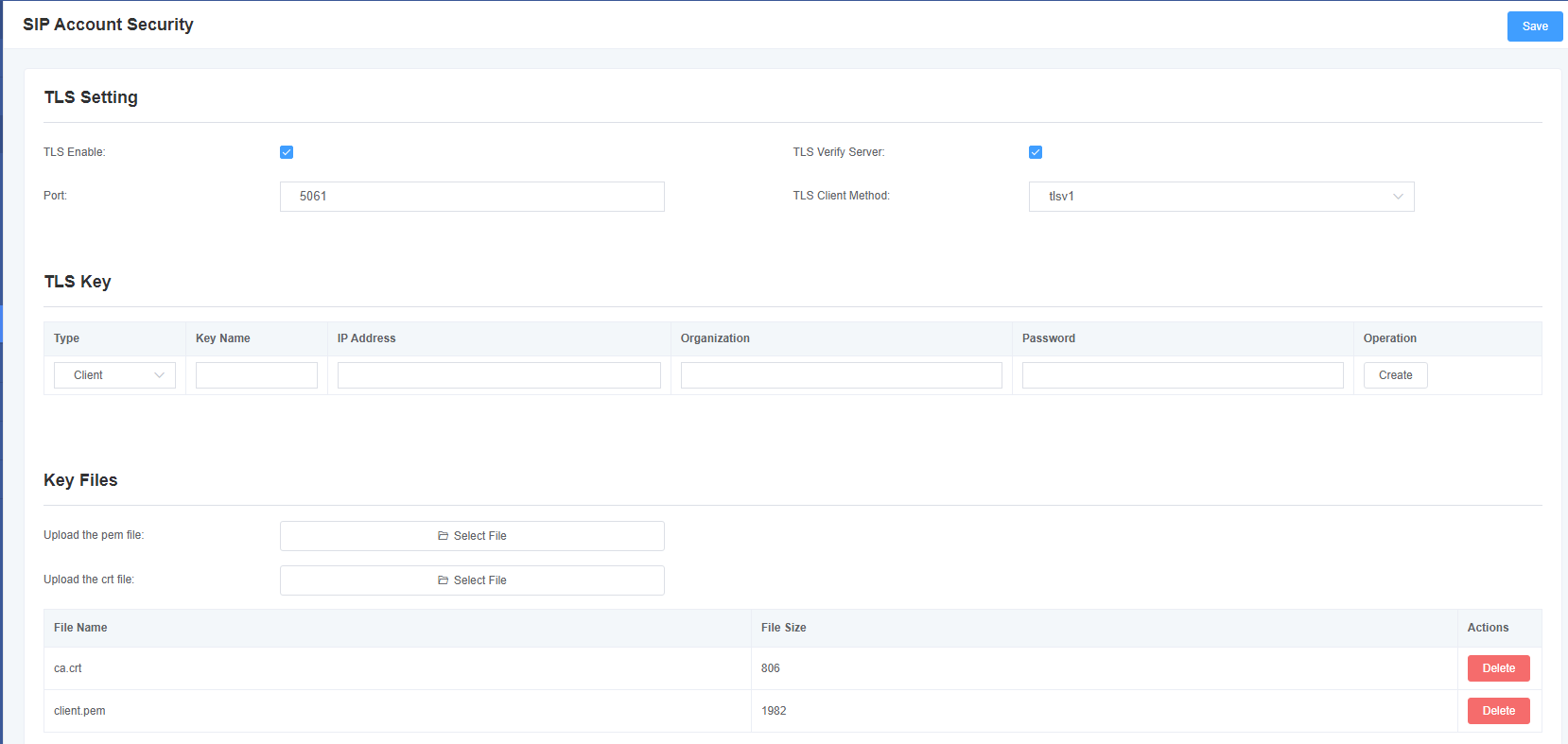
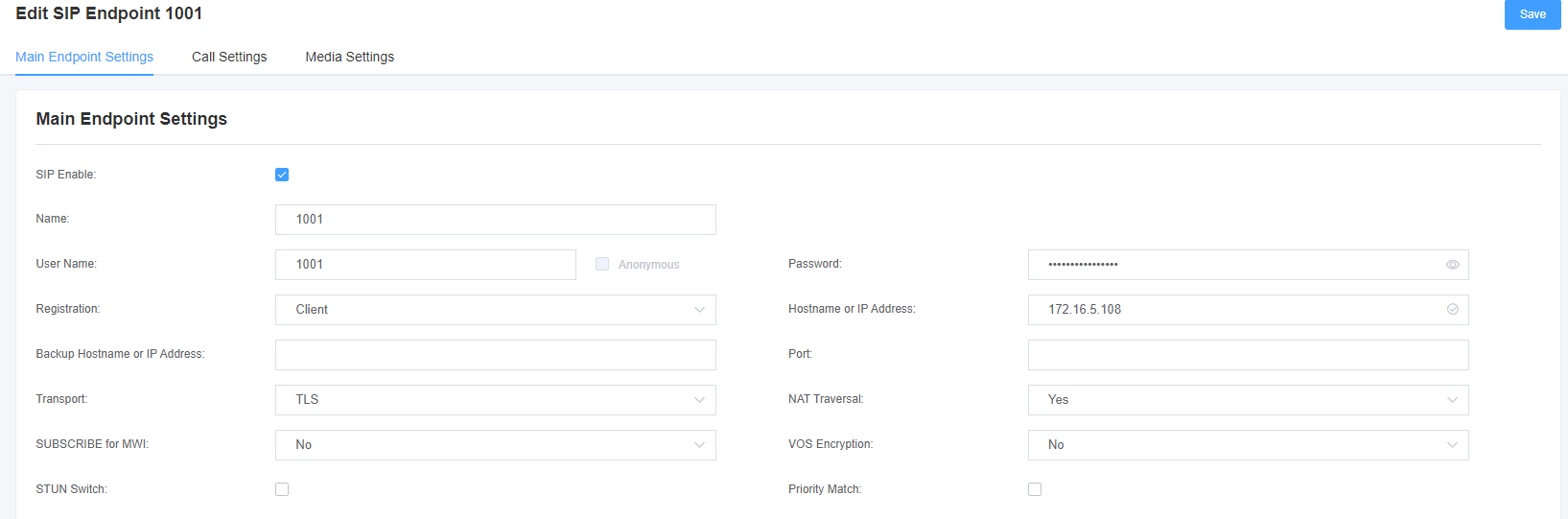
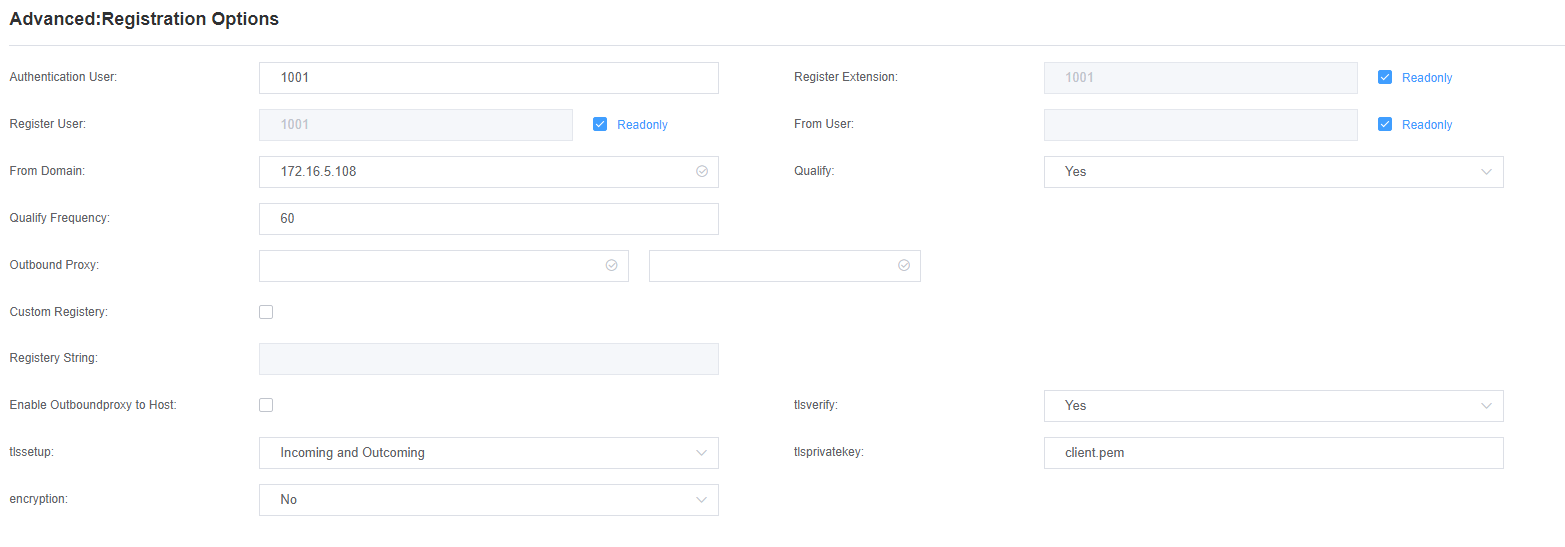
Step 4.Enable TLS on the Analog Gateway FXS, and upload the client key and certificate for extension 1001.
Go to VoIP->SIP Account Security, enable the TLS, and upload the client key and certificate for extension 1001.
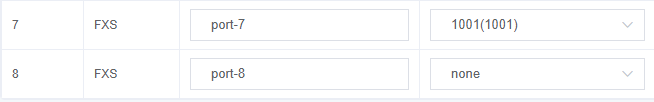
Step 5.Register extension 1001 on the Analog Gateway FXS, and bind it to the FXS port.
Step 6.Register extension 1002 on the softphone.