Navigation: Operation and Maintenance > Security Maintenance > Network Layer Security >
The unified gateway supports isolation of the management plane from the service plane to ensure the security of the system management plane.
![]()
Physical isolation is more secure and reliable; therefore, scheme 1 is recommended.
Scheme 1: Physical Isolation (for X1911/X1960/X1981 only)
Configure dual-network-port mode on the control board of the unified gateway to physically isolate the management plane from the service plane, which ensures that the management plane is invisible to the service plane. Figure 1 shows the network.
Figure 1 Network for physical isolation
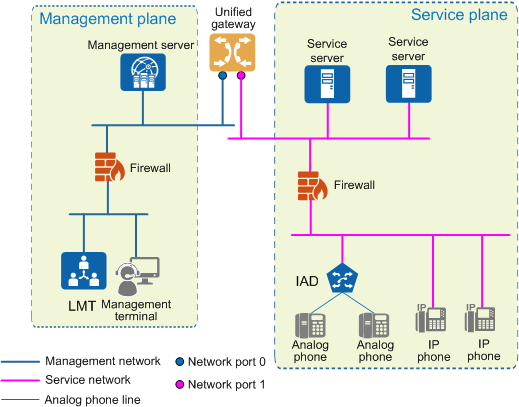
[Verification]
Attempt to access any IP address, protocol port, or URL of the management plane of the unified gateway from the service network. The access is expected to fail. For example, if you ping the IP address of network port 0, the ping operation is expected to fail.
Scheme 2: Firewall Policy Control
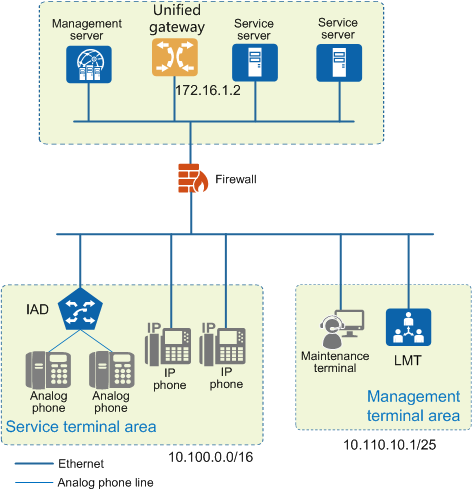
Configure the management plane access policy on the unified gateway and firewall. Such a policy specifies that only IP addresses in the management terminal area can access the URL or protocol port of the management plane. This ensures that the management entries are invisible to the service terminal area. Figure 2 shows the network.
Figure 2 Network for firewall policy control
Parent Topic: Network Layer Security